If you’re a business with an Internet connection, you’re being constantly bombarded by credible threats from around the world. Most people have never analyzed the data or experienced the sheer magnitude of this. In this short post I hope to demonstrate this.
As a use case, I’m using a Sophos XG firewall I setup recently for a customer. It’s not even in full production yet, and is only configured with basic firewall protection. What this means is I haven’t even configured any of its advanced features to detect more advanced threats. It’s essentially out of the box with default settings and only the most basic protection.
Actual Data from Analysis
For this analysis I looked at all the incoming traffic (There should be very little) and grabbed a random sampling of a 10 minute time span. The results are shocking.
Note: It’s easy to speculate that some sites have more and some sites have less threats. And the attacks are not constant. However, the point I am trying to demonstrate is that any site connected to the Internet is under constant threat of attack.
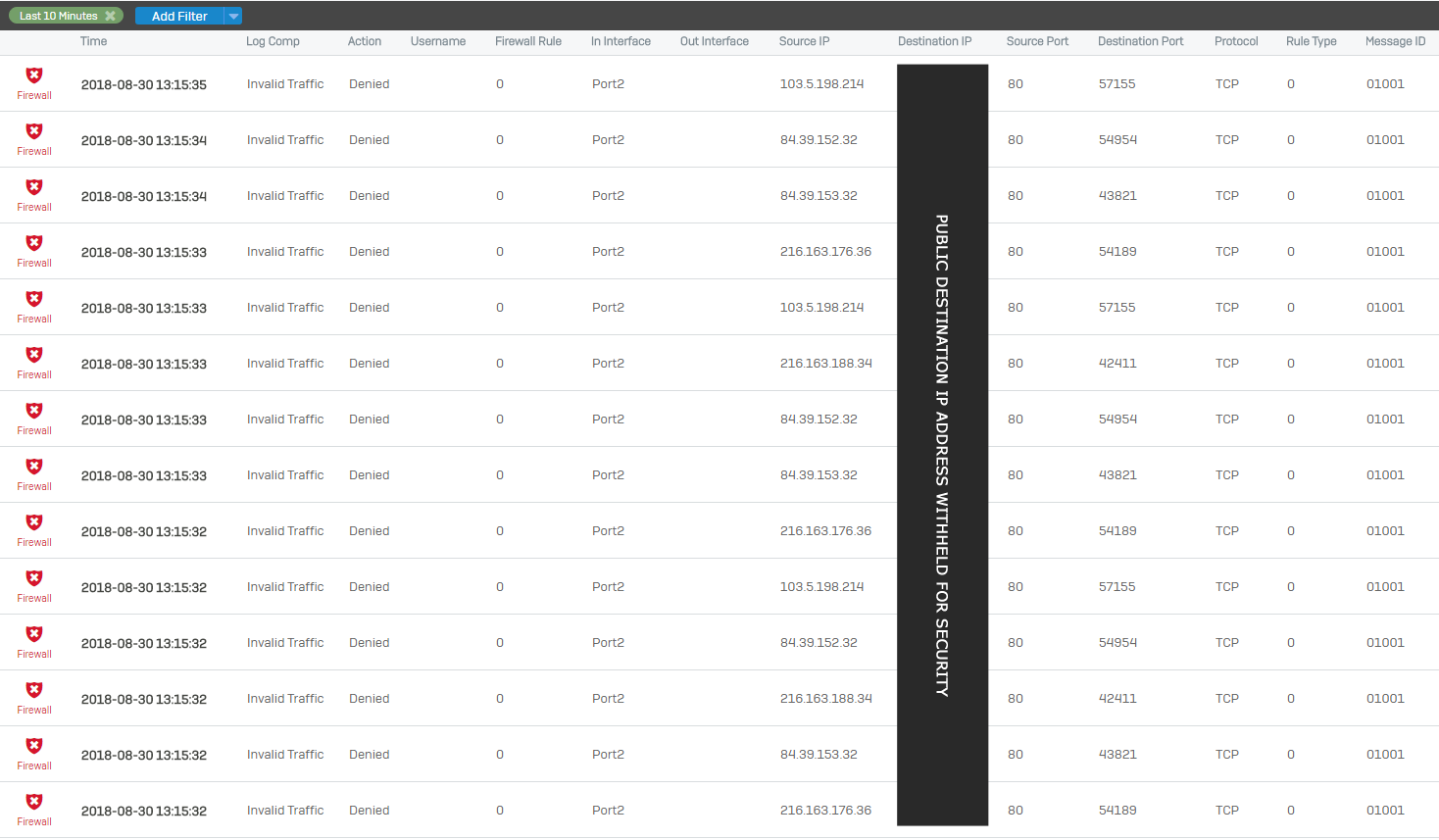
Actual Snippet of Blocked Report
Below is an actual snippet of traffic blocked. You can see that in the span of 2-3 seconds, at least 14 threats were blocked. The report shows the source IP as well as the destination port they are trying to connect to. This tells us a lot about what is going on.
Explanation
In this short snippet of 14 attacks, there were only 4 unique sources. This means that in two seconds, 4 remote systems tried to attack multiple times. Most likely they are performing a “Port Scan”. Once available ports are identified, further attacks are carried out specific to what they find.
From Wikipedia:
A port scanner is an application designed to probe a server or host for open ports. Such an application may be used by administrators to verify security policies of their networks and by attackers to identify network services running on a host and exploit vulnerabilities.
A port scan or portscan is a process that sends client requests to a range of server port addresses on a host, with the goal of finding an active port; this is not a nefarious process in and of itself. The majority of uses of a port scan are not attacks, but rather simple probes to determine services available on a remote machine.
Origination (Source) IP Addresses
The IP Addresses identified are as follows:
- 103.5.198.214 (3 Attempts)
- 84.39.152.32 (6 Attempts)
- 216.163.176.36 (3 Attempts)
- 216.163.188.34 (2 Attempts)
To further demonstrate the risk, and why it is important to protect against these threats, take a look at the source of the threat from a “location” perspective. Here’s an analysis of each of the 4 IP Addresses along with their location.
103.5.198.214
Location: Hong Kong
84.39.152.32
Location:Berlin, Germany
216.163.188.34
McLean, Virginia
216.163.176.36
McLean, Virginia
The location of the source traffic is not always significant, but here are some questions and thoughts that I have:
- Why is a system from Hong Kong trying to access my network?
- Why is a system from Berlin, Germany trying to access my network?
- Why is “ANYBODY” at this point trying to access my network?
- Even though two of the source IP Addresses are in from within the United States, I still question why they appear to be port scanning my system.
- Just because an address is from the US doesn’t mean it’s safe. A significant amount of malicious traffic originates in the United States.
- Do I have business partners or customers in any of these locations that should legitimately be accessing my system?
- Regardless of who/where the traffic is coming from, why is it trying to scan my network to identify open ports?
In Summary
Your business networks are under constant attack from outside sources. They’re trying to identify open ports and vulnerable systems that they can further exploit. It’s important to have a business class Firewall that can protect you from these threats. If you don’t have a firewall, or you’re using the default web routers from your Internet Provider that only do basic filtering, you’re leaving your company exposed.
Contact Marvin Huffaker if you’d like to learn how he can help protect your network from ever evolving threats.